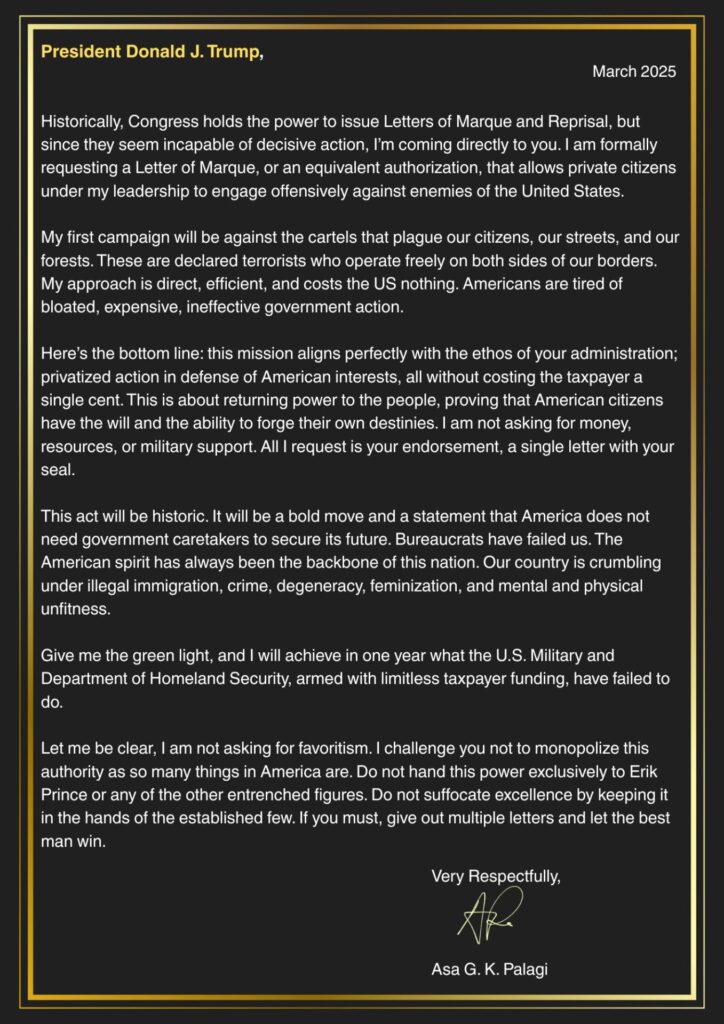
(YourDigitalWall Editorial):- Austin, Texas Mar 16, 2025 (Issuewire.com) – Asa Palagi, a U.S. military PSYOP officer and the founder of Notorious Security Group, has formally requested a Letter of Marque from President Donald J. Trump, seeking authorization to engage in direct action against the cartels operating along the U.S.-Mexico border. Palagi, who […]
Security
Auto Added by WPeMatico
(YourDigitalWall Editorial):- Brisbane, Queensland Jan 30, 2025 (Issuewire.com) – New Zealand is facing a rising wave of property crimes, including burglaries and unauthorized access, in both urban centers and rural communities. This increase in security risks has prompted a surge in demand for advanced and tailored security solutions. Amid this growing concern, Secure-as, […]
Alliance Training & Testing Unveils New Website with New Onsite Training Services at Client Hosted Locations with Service Area Pages. (YourDigitalWall Editorial):- Nashville, Tennessee Dec 21, 2024 (Issuewire.com) – Alliance Training and Testing, a leading provider of armed and unarmed security guard license training and certification services in Tennessee, is excited to […]
Business Email Fraud Compromise (BEC) is soaring and companies are being affected, BEC is an exploit in which the attacker gains access to a corporate email account and spoofs the owner’s identity to defraud the company or its employees, customers, or partners of funds. Typically, attackers request funds to […]